Radial Hierarchical Visualization: Difference between revisions
| Line 44: | Line 44: | ||
== Evaluation References == | == Evaluation References == | ||
A formal user study is pending as per April 2007. However, previous evaluations have been conducted, e.g.: | |||
*[Komlodi, et. al., 2005] Komlodi, A.; Rheingans, P.; Ayachit, U.; Goodall, J.R.; Joshi, A.; [http://ieeexplore.ieee.org/xpl/freeabs_all.jsp?arnumber=1566119 "A User-centered Look at Glyph-based Security Visualization"], Visualization for Computer Security, IEEE Workshops on Publication Date: 26 Oct. 2005 On page(s): 3- 3 | *[Komlodi, et. al., 2005] Komlodi, A.; Rheingans, P.; Ayachit, U.; Goodall, J.R.; Joshi, A.; [http://ieeexplore.ieee.org/xpl/freeabs_all.jsp?arnumber=1566119 "A User-centered Look at Glyph-based Security Visualization"], Visualization for Computer Security, IEEE Workshops on Publication Date: 26 Oct. 2005 On page(s): 3- 3 | ||
Revision as of 16:30, 26 April 2007
Authors
Schreck, Tobias
Short Description
Suitable Data Types
Suitable data types for this information visualization technique are Internet Protocol packets.
Figures
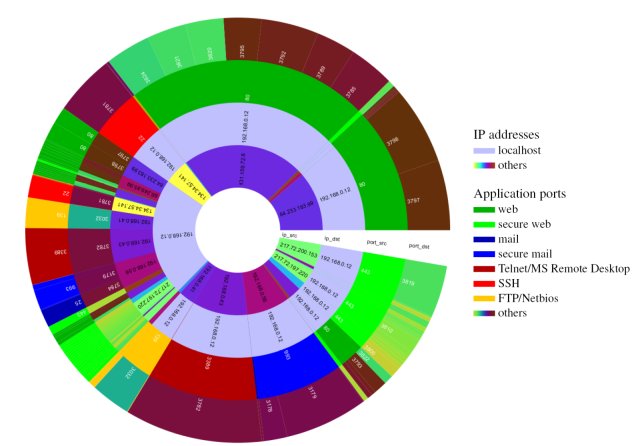
The Radial Traffic Analyzer visualizes network traffic using a radial hierarchical layout. The radial visualization was chosen to avoid the user assigning more importance to an item due to its position on the left or on the right. In the default configuration, the Radial Traffic Analyzer uses four concentrical rings, each one representing an attribute of the transferred packets.
The innermost ring shows the source IP adress contained in the packet, the second ring shows the destination IP, the third ring shows the source port number, and the outermost ring the destination port number. The size of a circle segment specifies the portion of the total traffic payload. To improve readability entries with the same values (same IP or same port number) are drawn using the same colour. Entries of popular port numbers appear in unique colours (e.g. green is always used for port 80 - HTTP). Traffic over secured channels is shown in brighter colours, whereas traffic over unsecured channels is usually displays in darker colour.
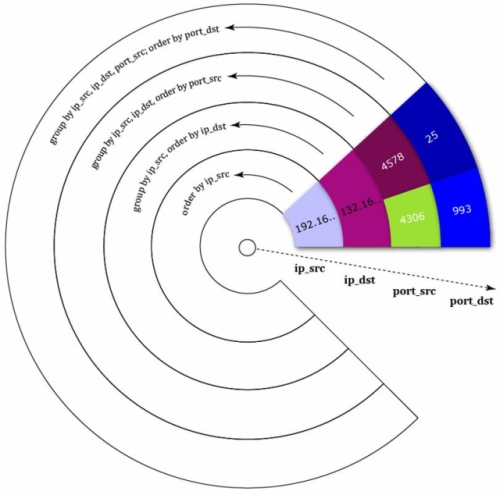
The values on each ring are grouped by the attributes on the inner rings. Values are sorted on a ring. The next figure shows the design rationale:
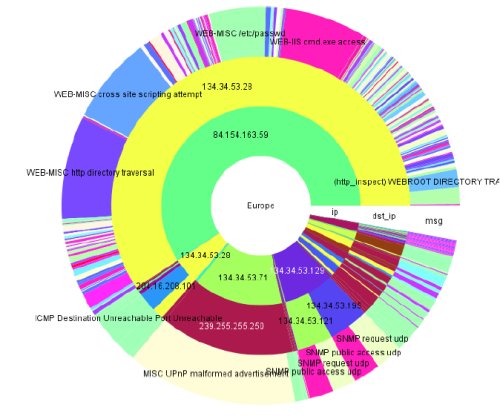
The Radial Traffic Analyzer allows a variety of user interaction. Entries and their associated traffic can be filtered by single-clicking a circle segment. The order of the rings can be adapted to the users' needs, as well as the number of the rings, or their attributes. For example, the Radial Traffic Analyzer can be configured to display security alerts generated by an intrusion detection system:
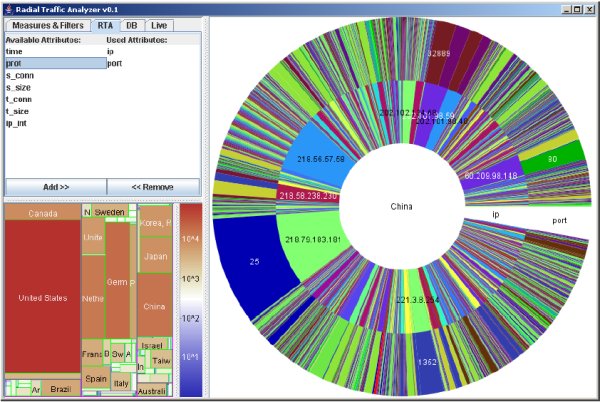
As seen in the figure above, the innermost circle can be used to limit the source of network traffic to one specified country. For this purpose, the Radial Traffic Analizer uses the Maxmind’s GeoIP Database to evaluate the geo-location information. Geographical information is arranged on a treemap using the HistoMap algorithm; each geographical unit is matched to a rectangle. The amount of traffic determines the rectangle size.
Evaluation
Up to April 2007 there hasn't been any evaluations or implementations of the Radial Traffic Analyzer.
References
- [Keim, et al., 2006] Keim, D.A.; Mansmann, F.; Schneidewind, J.; Schreck, T.; "Monitoring Network Traffic with Radial Traffic Analyzer", Visual Analytics And Technology, 2006 IEEE Symposium On Oct. 2006 Page(s):123 - 128
Evaluation References
A formal user study is pending as per April 2007. However, previous evaluations have been conducted, e.g.:
- [Komlodi, et. al., 2005] Komlodi, A.; Rheingans, P.; Ayachit, U.; Goodall, J.R.; Joshi, A.; "A User-centered Look at Glyph-based Security Visualization", Visualization for Computer Security, IEEE Workshops on Publication Date: 26 Oct. 2005 On page(s): 3- 3
- [Stasko, et. al., 2000] Stasko, J.; Zhang, E.; "Focus+context display and navigation techniques for enhancing radial, space-filling hierarchy visualizations", Information Visualization, 2000. InfoVis 2000. IEEE Symposium on Publication Date: 2000 On page(s): 57-65